Brief Introduction to Email-Worm.Win32.Brontok.q
Email-Worm.Win32.Brontok.q is classified as Trojan horse which is designed by cyber criminals to promote their evil aims by stealing useful information stored in the target computer even destroying the computer if they want.
Ways of Email-Worm.Win32.Brontok.q Comes into Your PC
Generally speaking, this Trojan horse sneaks into your computer without your knowledge and awareness. It usually takes advantage of being bundled with spam email attachments. As soon as you open the attachments, this Trojan will be downloaded into your computer. Downloading freeware that contain its codes, clicking malicious pop-ups, browsing suspected websites, or opening intrusive links also can download this Trojan to your computer.
Dangerous of Email-Worm.Win32.Brontok.q
Once loaded, this Trojan infection will firstly hide itself as a normal program in your system files. While being executed, it is capable of setting a backdoor for cyber criminals to take control of computer remotely. Once controlled, the cyber criminals will have the chance to monitor what you are doing in the computer and collect your valuable information. As a result, the cyber criminals can easily steel your important information and sensitive privacy such as usernames, passwords, credit card details and bank account information.
Moreover, this Trojan infection enables to disable or lock some normal programs to run by planting several malicious rootkits into your operating system. Those small rootkits can give false commands and instructions to your computer system. As soon as the operating system receives those wrong commands and follows the instructions to run, some programs on your computer will run in disorder and even cause fatal system errors.
Gradually, your computer will result in poor performance while being infected with this Trojan horse for a long time. For instance, your computer will run in slower speed, take a longer time to turn on or shut down, get frozen up easily while loading web pages or opening programs, and even crash down suddenly.
To summarize, this Email-Worm.Win32.Brontok.q is a hazardous Trojan horse that is able to conduct a series of damaging actions to cause large amounts of problems to your computer security and your online safety. It is strongly recommended to remove Email-Worm.Win32.Brontok.q Trojan horse as soon as possible once it is found before it causes further damages.
Removal Guide for Email-Worm.Win32.Brontok.q
Instruction A: Remove Email-Worm.Win32.Brontok.q Trojan Horse Manually
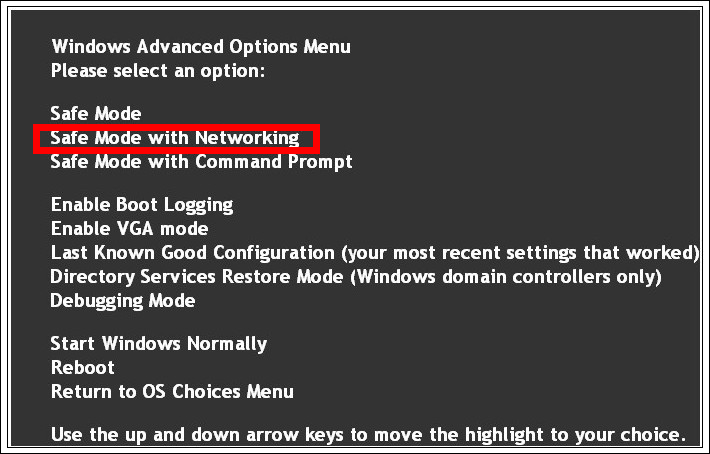
Step 1. Reboot your computer into Safe Mode with Networking
Restart your computer and keep pressing F8 key until Windows Advanced Options Menu shows up, then using arrow key to select Safe Mode with Networking from the list and press Enter to get into that mode.
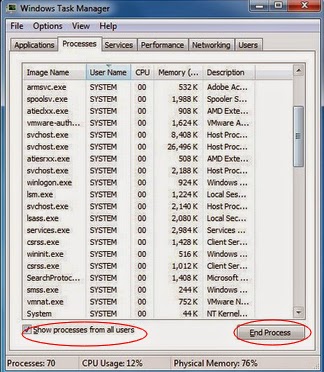
Press Ctrl+Alt+Del keys together to launch Window Task Manager, then end the suspicious processes.
%UserProfile%\Programs\AppData\[Random Charateristc].exe
%UserProfile%\Programs\Temp\[Random Charateristc].dll
%UserProfile%\Programs\AppData\roaming\[Random Charateristc].dll
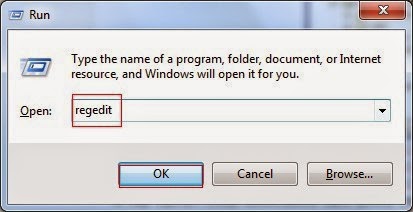
Step 4. Delete associated registry entries
Hit Win+R keys and then type regedit in Run box and click on OK to open Registry Editor.
When the Registry Editor shows, find out and delete the below files.
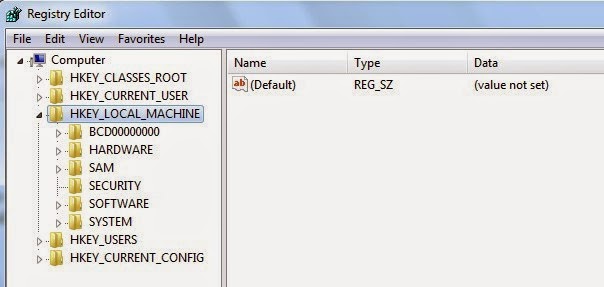
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run""= "%AppData%\.exe"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes"="random;"
Note: When you apply this manual removal guide, you need to be very careful about each step. One mistake would delete the important system file. Therefore, be careful.
Instruction B: Remove Email-Worm.Win32.Brontok.q Trojan Horse Automatically
Step 1. Install SpyHunter
1. Download SpyHunter here, or click the below button to download the file.
2. Double click on it to install it.
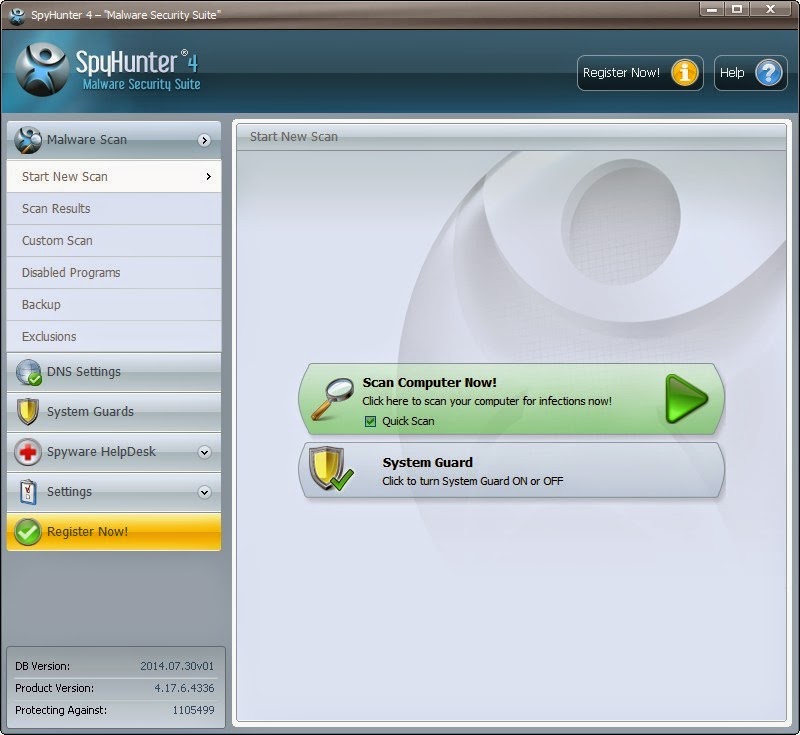
1. If SpyHunter does not open automatically after its installation, double click on its desktop shortcut to open the program. If you would like a quick scan on your computer, please tick mark on Quick Scan, otherwise do not tick it. Then click on the Scan Computer Now! button to run a scan on your computer.
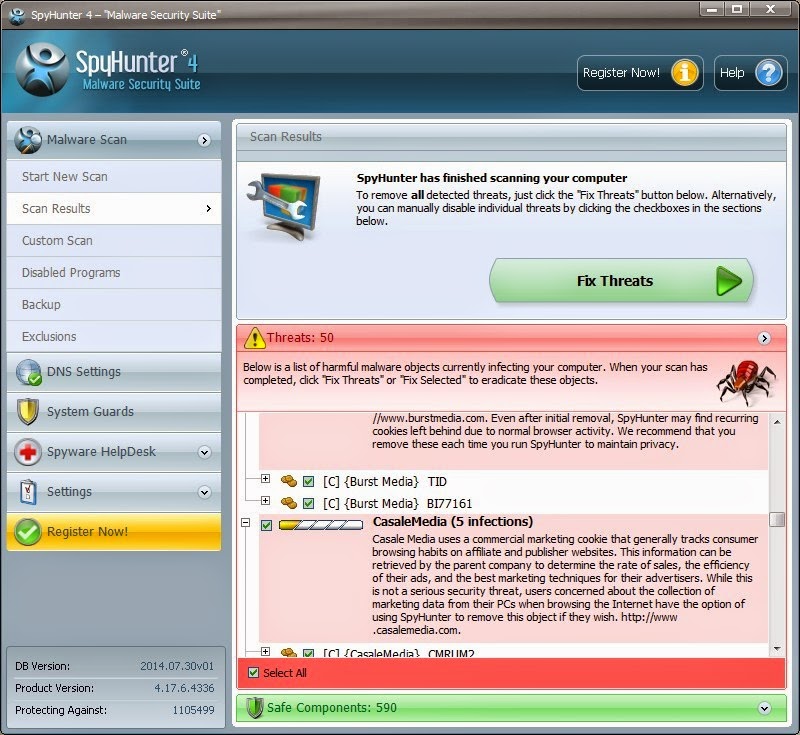
2. When the scan is done, you can see that Email-Worm.Win32.Brontok.q Trojan horse is successfully detected. Then click on Fix Threats.
Note: For the people who are not familiar with computer knowledge, the automatic removal is much more easier than the manual one. It is recommended to use SpyHunter to delete Email-Worm.Win32.Brontok.q Trojan horse or when you face any malicious virus, it will remove the threats completely. Click here to download SpyHunter freely.
Step 3. Clean Out the Trash
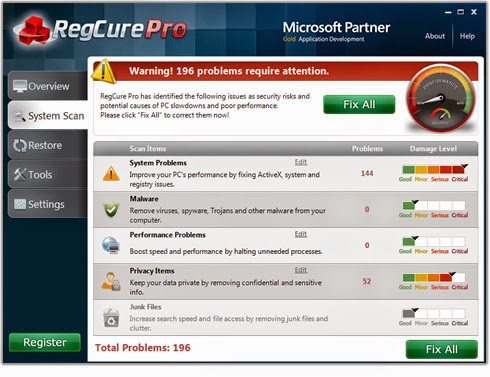
If you want to clean out the trash produced by Email-Worm.Win32.Brontok.q or uninstalling programs, manage your startup items and optimize your computer performance, it is recommended to apply RegCure Pro to help you. Here shows how it works.
1. Freely download RegCure Pro here, or click the below button to download the file.
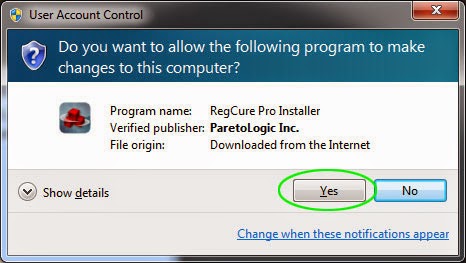
2. Double click on its application and click the Yes button to install the program step by step.
3. After the installation is complete, open the program and scan your system for unnecessary files and invalid registry entries. That will take some time for the first scanning. Please wait while the program scans your system for performance problems.

4. When the System Scan is done, click Fix All button to correct all the security risks and potential causes of your computer slow performance.


No comments:
Post a Comment